The Teams
A comprehensive guide to the rainbow of cybersecurity roles that protect our digital world
The Same Team
A Cybersecurity Educational Movement
"It's Time To Get On The Same Team" - Semper Fortis. Always Strong.

United We Stand
Together, we emerge into something greater than the sum of all of our parts.
Before we dive into the specialized roles—the reds, blues, purples, and all the colors of the cybersecurity rainbow—we must first acknowledge a fundamental truth: we are all on the same team.
The Same Team is not just another color in the spectrum. It is the canvas upon which all other teams paint their expertise. It represents the universal role that anyone can play in cybersecurity, regardless of technical background, organizational affiliation, or professional title. It is the recognition that security is everyone's responsibility, and that every contribution—no matter how small—strengthens our collective defense.
What is The Same Team?
- A Movement: The Same Team is a grassroots cybersecurity educational movement that empowers individuals to contribute to digital security, regardless of their role or expertise level.
- A Mindset: It embodies the belief that cybersecurity is not the sole domain of specialists, but a shared responsibility that requires collaboration across all boundaries.
- A Call to Action: The Same Team invites everyone—from students to executives, from developers to end users—to learn, share, and contribute to our collective cyber resilience.
In a world where cyber threats transcend borders, industries, and technical domains, we cannot afford to work in silos. The adversaries we face are coordinated, persistent, and increasingly sophisticated. Our response must be equally unified. The Same Team recognizes that:
- Every person who practices good password hygiene strengthens the chain
- Every developer who writes secure code prevents future vulnerabilities
- Every educator who teaches security awareness creates a more resilient community
- Every organization that shares threat intelligence helps protect others
- Every individual who reports suspicious activity becomes a sentinel
"Alone we can do so little; together we can do so much. In cybersecurity, this is not just inspiration—it is survival."
How You Can Join The Same Team
Learn & Share
Educate yourself about cybersecurity basics and share that knowledge with others. Every person you teach improves state of security for everyone else.
Practice Security
Implement security best practices in your daily digital life. Use strong passwords, enable MFA, and stay vigilant against phishing.
Build Community
Connect with others interested in cybersecurity. Join forums, attend meetups, and participate in educational initiatives like Unitium.One.
Contribute
Share your experiences, report vulnerabilities responsibly, and contribute to open-source security projects. Every contribution matters.
The specialized teams you'll read about below—Red, Blue, Yellow, Orange, Green, Purple, White, Black, and Gold—each play crucial roles in the cybersecurity ecosystem. But they all operate under the umbrella of The Same Team. They may have different tools, different perspectives, and different objectives, but they share a common mission: protecting our digital world.
As you explore the roles and responsibilities of each team, remember that you don't need to be a penetration tester, a SOC analyst, or a security architect to make a difference. You just need to be willing to learn, to care, and to act. That's what it means to be on The Same Team.
Let's Get On The Same Team
Because in the end, we're not just defending systems—we're defending each other.
Semper Fortis. Always Strong.
The Rainbow of Cybersecurity Teams
The Cybersecurity Color Wheel
A visual representation of the diverse roles that make up our unified security ecosystem
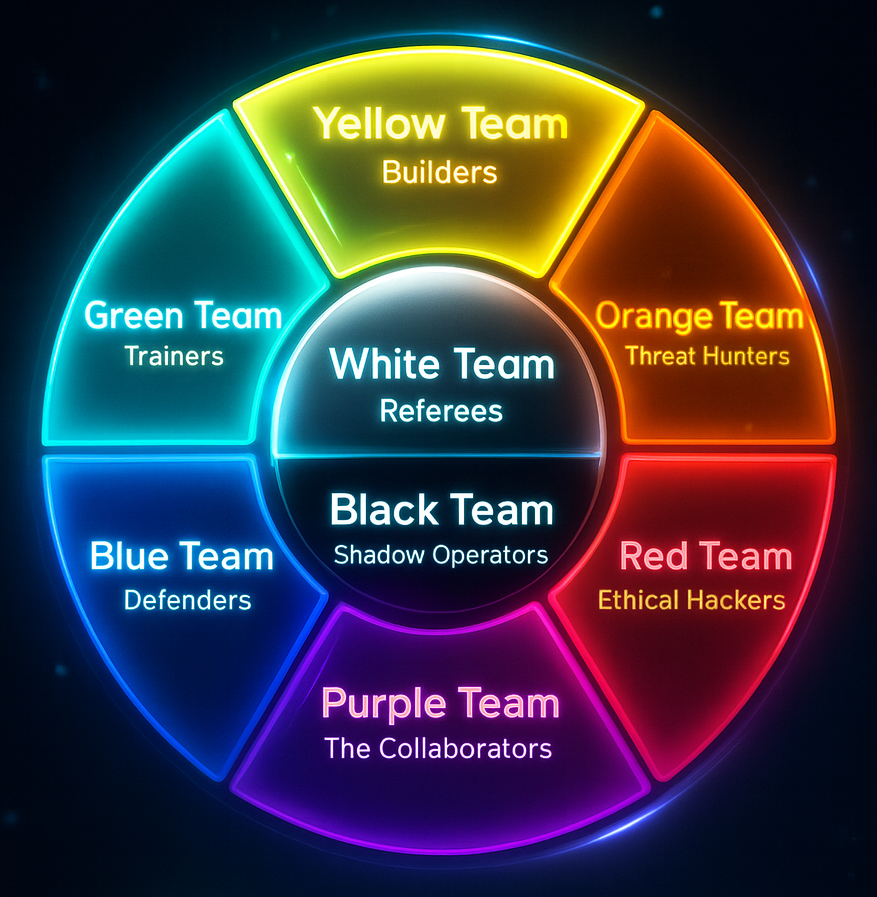
Click the download button to save this color wheel for reference
In the symphony of cybersecurity, each team plays a distinct instrument, contributing unique melodies that harmonize into a comprehensive defense. Like colors in a rainbow, these teams blend and overlap, creating new capabilities and perspectives that strengthen our collective security posture.
This guide explores the full spectrum of cybersecurity teams—from the foundational primary colors (Red, Blue, Yellow) to the collaborative secondary colors (Orange, Green, Purple) and the specialized governance teams (White, Black, Gold). Understanding these roles and how they interact is essential for building resilient security programs in today's threat landscape.
Key Insight for Learners
The most effective cybersecurity professionals don't just master one team's skills—they understand how all teams interconnect. A Red Teamer who understands Blue Team challenges writes better reports. A developer who thinks like an attacker builds more secure code. A defender who appreciates the builder's constraints creates more practical security controls.
Your learning strategy: As you explore each team, ask yourself: "How does this team's work affect the others? Where do they collaborate? What can I learn from their perspective?"
"The strength of the team is each individual member. The strength of each member is the team." — Phil Jackson
The primary colors of cybersecurity—Red, Blue, and Yellow—form the foundation upon which all other teams are built. Like primary colors in art, these teams cannot be created by mixing others; they are fundamental and essential.
Red Team: The Adversary Simulators

Red Team in Action
Simulating real-world attacks to strengthen defenses
Red Teams are the ethical hackers, the adversary simulators who think like attackers to test and strengthen an organization's defenses. They operate in the shadows, probing for weaknesses, exploiting vulnerabilities, and demonstrating what a real attacker could accomplish.
"We become the storm to reveal where the shelter leaks, finding weaknesses before the real tempest arrives."
Modern Red Teams go far beyond simple penetration testing. They emulate specific threat actors, combining technical exploits with social engineering, physical security testing, and persistence techniques. Their goal is not just to find vulnerabilities, but to demonstrate realistic attack scenarios and their potential business impact.
High-Leverage Learning Points
- Think in attack chains, not single vulnerabilities: Real attackers chain multiple weaknesses together. Learn to see how a minor information disclosure + weak authentication + misconfigured permissions = complete compromise.
- Master the art of living off the land: The best Red Teamers use built-in tools and legitimate credentials. Study PowerShell, bash, and native OS capabilities more than custom exploits.
- Communication is your superpower: A Red Teamer who can't explain findings to non-technical stakeholders is only half as effective. Practice translating technical risks into business impact.
- Ethical boundaries are non-negotiable: The line between Red Team and criminal is defined by authorization, scope, and intent. Never cross it, even when you could.
- Conducting penetration tests and security assessments
- Simulating advanced persistent threats (APTs)
- Social engineering and phishing campaigns
- Developing custom exploits and attack tools
- Physical security testing
- Operate with clear scope and authorization
- Emulate real-world threat actors
- Document findings with evidence
- Prioritize by risk and exploitability
- Provide actionable remediation steps
- Metasploit, Cobalt Strike
- Burp Suite, OWASP ZAP
- Nmap, Nessus
- Custom exploit frameworks
- Social engineering toolkits
Blue Team: The Defenders

Blue Team Operations Center
The nerve center of defensive security operations
Blue Teams are the guardians of the digital realm, the defenders who protect systems, detect threats, and respond to incidents. They are the watchful sentinels who never sleep, constantly monitoring for signs of intrusion and working to strengthen defenses against an ever-evolving threat landscape.
"In the silent digital night, we are the watchful guardians, ever vigilant against the shadows that seek to breach our walls."
Modern Blue Teams have evolved far beyond simple firewall management. They leverage advanced analytics, threat intelligence, and automation to detect and respond to threats at machine speed. They operate with an "assume breach" mentality, focusing on rapid detection and containment rather than perfect prevention.
- Implementing security controls and defenses
- 24/7 security monitoring and threat detection
- Incident response and recovery
- Vulnerability management and patching
- Security awareness training
- Assume breach mentality
- Defense in depth strategy
- Automate routine security tasks
- Comprehensive logging and monitoring
- Regular incident response drills
- SIEM platforms (Splunk, ELK)
- IDS/IPS systems
- EDR solutions
- SOAR platforms
- Vulnerability scanners
Yellow Team: The Builders

Yellow Team at Work
Building secure systems from the ground up
Yellow Teams are the builders—the developers, programmers, software engineers, and architects who create the systems, applications, and infrastructure that power our digital world. They are the foundation upon which all security efforts are built, for a system designed without security in mind is a fortress built on sand.
"We lay the foundation stones of the digital realm, ensuring that every line of code, every architecture decision, contributes to a structure that can withstand the test of time and threat."
The Yellow Team's role is often underappreciated in cybersecurity discussions, yet they are fundamental. Every vulnerability that Red Teams find, every incident that Blue Teams respond to, often traces back to decisions made during the building phase. When Yellow Teams prioritize security from the start, they prevent countless future problems.
- Designing and building secure systems
- Developing applications and infrastructure
- Creating network architectures
- Implementing business requirements
- Maintaining and updating systems
- Security by design principles
- Follow secure coding standards
- Regular code reviews
- Threat modeling during design
- Minimize attack surface
- IDEs and development frameworks
- Version control systems (Git)
- CI/CD pipelines
- Architecture design tools
- Documentation platforms
Secondary colors emerge when primary colors blend together, creating new capabilities and perspectives. Orange, Green, and Purple teams represent the collaborative spirit of modern cybersecurity, where different specialties work together to create something greater than the sum of their parts.
Note: Some organizations define Orange and Green teams as specialized builders (Secure Builders and DevSecOps Champions), while others consider them Threat Hunters (Orange) and Trainers (Green). Under some organizational models, educational platforms like Unitium.One would fall under Green Team operations.
Orange Team: The Threat Hunters
(Red + Yellow)
Orange Team Threat Hunting
Proactively searching for hidden threats
Orange Teams blend the offensive mindset of Red Teams with the analytical capabilities of Yellow Teams. They are proactive threat hunters who search for signs of compromise within systems, identifying threats that have evaded traditional defenses. By combining attacker knowledge with systematic analysis, Orange Teams find the needles in the haystack before they cause damage.
"We hunt with the mind of an attacker and the precision of an analyst, finding threats that hide in the shadows before they strike."
Under some organizational models, Orange Teams focus on secure development and training developers on attack methods. Regardless of the specific definition, the Orange Team philosophy remains the same: combine offensive knowledge with proactive analysis to stay ahead of threats.
- Proactive threat hunting in enterprise environments
- Analyzing indicators of compromise (IOCs)
- Identifying advanced persistent threats (APTs)
- Developing threat hunting hypotheses and methodologies
- Secure development training (some organizational models)
- Threat intelligence platforms
- SIEM and log analysis tools
- Endpoint detection and response (EDR)
- Network traffic analysis tools
- Malware analysis sandboxes
Green Team: The Trainers
(Blue + Yellow)
Green Team Education
Building security knowledge across the organization
Green Teams merge the defensive expertise of Blue Teams with the building and teaching capabilities of Yellow Teams. They focus on training and education, helping others understand and implement security best practices. By spreading security knowledge throughout the organization, Green Teams create a culture where everyone contributes to defense.
"We plant the seeds of security knowledge in every mind, nurturing a community that grows stronger, wiser, and more resilient with each lesson learned."
Educational platforms like Unitium.One operate as Green Team initiatives, spreading security knowledge and building a more security-aware community. Under some organizational models, Green Teams focus on DevSecOps, integrating security throughout the software development lifecycle.
- Security awareness training for all employees
- Developing security education programs and curricula
- Creating security documentation and best practice guides
- Conducting security workshops and hands-on training
- DevSecOps integration (some organizational models)
- Learning management systems (LMS)
- Security training platforms and simulators
- Phishing simulation tools
- Documentation and knowledge base systems
- CI/CD security integration tools
Purple Team: The Collaborative Force
(Red + Blue)
Purple Team Collaboration
Where offensive and defensive expertise converge
Purple Teams represent the harmonious collaboration between Red and Blue Teams, creating a feedback loop that continuously improves security posture. They facilitate knowledge transfer, validate detection capabilities, and ensure that offensive findings translate into defensive improvements.
"In the harmony of offense and defense, we find the true melody of security—a continuous dance of learning and adaptation where yesterday's attack becomes today's defense."
Purple Team exercises range from focused sessions testing specific detection capabilities to comprehensive scenarios simulating full attack chains. The key is maintaining open communication and a shared learning mindset rather than a competitive approach.
- Facilitating knowledge transfer between red and blue teams
- Conducting joint security exercises
- Validating detection capabilities in real-time
- Improving incident response procedures
- Creating feedback loops for continuous improvement
- Threat emulation platforms
- MITRE ATT&CK framework
- Breach and attack simulation tools
- Collaborative documentation systems
- Shared dashboards and metrics
Beyond the primary and secondary colors, three specialized teams provide governance, physical security, and crisis management capabilities. White, Black, and Gold teams ensure that cybersecurity operations are conducted ethically, comprehensively, and with proper oversight.
White Team: The Referees

White Team Oversight
Establishing rules and ensuring ethical operations
White Teams serve as the referees and governance body for cybersecurity operations. They establish rules of engagement, define methodologies, oversee testing processes, and ensure that all security activities are conducted ethically, legally, and in alignment with organizational objectives.
"We are the guardians of the rules, ensuring that in our quest to strengthen defenses, we never lose sight of ethics, legality, and the greater good we serve."
Without White Teams, security operations risk becoming chaotic or crossing ethical boundaries. They provide the structure, oversight, and accountability that allow other teams to operate effectively while maintaining trust and compliance.
- Establishing rules of engagement for security testing
- Defining testing methodologies and standards
- Overseeing security exercises and operations
- Ensuring compliance with regulations and policies
- Mediating disputes and resolving conflicts
- Scope definition and authorization
- Risk assessment and mitigation planning
- Exercise coordination and timing
- Stakeholder communication
- Post-exercise debriefing and reporting
Black Team: The Physical Security Specialists

Black Team Operations
Testing physical security and providing threat intelligence
Black Teams bridge the gap between cyber and physical security, recognizing that digital defenses mean little if an adversary can simply walk through the front door. They conduct physical security assessments, test access controls, and provide updated cyber threat intelligence that informs both digital and physical security strategies.
"In the shadows between the digital and physical realms, we test the boundaries that others forget, reminding all that security is not just about firewalls and code—it's about doors, locks, and human vigilance."
Black Teams understand that many of the most devastating breaches begin with physical access—a tailgated door, a stolen laptop, a compromised badge. By testing these vectors, they ensure that organizations maintain comprehensive security that addresses both digital and physical threats.
- Physical security assessments and penetration testing
- Testing access controls and badge systems
- Social engineering via physical presence
- Providing cyber threat intelligence updates
- Assessing surveillance and monitoring systems
- Tailgating and unauthorized access attempts
- Badge cloning and credential theft
- Lock picking and physical bypass techniques
- Dumpster diving and information gathering
- Surveillance detection and evasion
Gold Team: The Crisis Managers

Gold Team Tabletop Exercise
Testing crisis management and strategic response
Gold Teams conduct tabletop exercises and simulations that test an organization's crisis management capabilities. Composed of business leaders and management-level stakeholders from IT, legal, finance, communications, and the C-suite, Gold Teams simulate realistic cyber incident scenarios to identify gaps in crisis response plans and improve organizational resilience.
"When the storm arrives, technical skills alone will not save us. We must be prepared to lead, to communicate, to make difficult decisions under pressure. Gold Team exercises forge that readiness in the crucible of simulation."
Gold Team exercises bridge the gap between technical incident response and strategic crisis management. They ensure that when a real incident occurs, leadership knows how to respond, who to contact, what to communicate, and how to minimize business impact while technical teams work to contain and remediate the threat.
- Conducting tabletop exercises and crisis simulations
- Testing crisis management and communication plans
- Identifying gaps in incident response procedures
- Training leadership on cyber incident response
- Improving organizational cyber resilience
- Realistic cyber incident scenarios
- Decision-making under pressure
- Stakeholder communication strategies
- Legal and regulatory considerations
- Business continuity and recovery planning
Learn More: Resources & References
This guide synthesizes insights from leading cybersecurity resources and thought leaders. To deepen your understanding of cybersecurity teams, explore these excellent references:
A comprehensive exploration of the full spectrum of cybersecurity teams, from primary colors to specialized roles. Essential reading for understanding team dynamics.
Read ArticlePrivasec Global's detailed breakdown of cybersecurity team roles, including governance and specialized teams. Excellent for understanding organizational structures.
Read ArticleTechopedia's accessible introduction to offensive and defensive security roles, perfect for those new to cybersecurity team concepts.
Read ArticleThe industry-standard knowledge base of adversary tactics and techniques, essential for Red, Blue, and Purple Team operations.
Visit FrameworkThe Path Forward: Together on The Same Team
We've journeyed through the rainbow of cybersecurity teams—from the foundational Red, Blue, and Yellow, through the collaborative Orange, Green, and Purple, to the specialized White, Black, and Gold. Each team brings unique capabilities, perspectives, and expertise to the eternal challenge of securing our digital world.
But as we close this guide, let us return to where we began: The Same Team. For all the specialization, all the distinct roles and responsibilities, all the different colors in the spectrum—we are united by a common purpose. We stand together against threats that know no boundaries, that respect no borders, that target the vulnerable regardless of their defenses.
"In the digital age, our collective security is only as strong as our weakest link. But when we work together, when we share knowledge, when we support each other—there are no weak links, only a chain of steel forged in the fire of collaboration."
The teams described in this guide represent the professional specializations within cybersecurity. But The Same Team represents something more fundamental: the recognition that security is everyone's responsibility, that every contribution matters, and that together we are stronger than any threat.
Your Role on The Same Team
You don't need to be a Red Team operator or a Blue Team analyst to make a difference. You just need to:
As you continue your cybersecurity journey—whether you aspire to join a Red Team, strengthen Blue Team defenses, build secure systems as part of a Yellow Team, or simply want to be a more security-conscious digital citizen—remember that you are not alone. You are part of a global community of individuals who care about security, who work to protect others, and who believe that together, we can build a safer digital world.
Help Us Improve This Guide
This guide is a living document, and we welcome contributions from the community. If you have insights, experiences, or suggestions for improving our coverage of any cybersecurity team, please reach out. Together, we can create the most comprehensive resource on cybersecurity teams available.
Send your ideas, discussion points, and feedback to August@Unitium.One. Let's work together to educate and empower the next generation of cybersecurity professionals.